why do we need https?
Normal http does not contain validation. In the real world, when we use online banking or any website, which need to input our private information, these information need to store securely and send to server. Otherwise, pure information will be stolen while connecting to proxy server. Then, Https is needed to protect security of information.
user information --> proxy server(attacked) --> target server
how can https protect security?
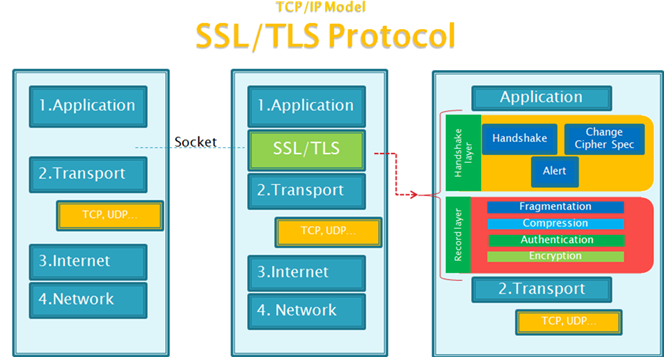
Base on Internet Protocol Suit, TCP is the next connection of http, which is to transform application data. Https is that http added one layer of SSL or TSL protcol to encrypt data, then send to TCP.
encrypt data methods
Https uses mixed two methods to encrypt data, symmetric-key algorithm and asymmetric key encryption.
Symmetric-key algorithm means client and server share common key to encrypt and decrypt data. However, if client uses this key to encrypt data and sends encrypted data with this key to server, then it is possible to be attacked, which means encrypted data will be decrypted by whoever gets this key.
Asymmetric key encryption means there are two keys, namely, private key and public key. Public key is everyone can see it, while private key is only server can see. In the process of SSL/TSL, client starts handshaking with server. Server will respond with certificate to client, such CA contains public key. Client needs to verify this certificate, then use public key to encrypt user private data, send to server. Private key will be used to decrypt data in the server side, and encrypt request info back to client side. Since public key is public and can decrypt data from server side, it could be attacked by others. Meanwhile, asymmetric key encryption is lower comparing with symmetric-key algorithm. Therefore, the combination of two methods is to increase efficiency of data transformation.
Based on Asymmetric key encryption, when client sends ClientHello request, it will generate random number, which sends along with request. ServerHello response will contain random number, which will be both in client and server sides. After verification of certificate, the third random number is generated by client and encrypted by public key from certificate, and such number will be sent to server. Thus, both client and server have three random number, then they can generate their common key for communication. The handshaking layer is done.

With this new key, communication between client and server is to record layer, which is to use basic http protocol.